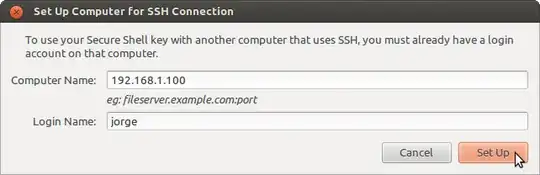
The ssh-copy-id command (in the openssh-client package and installed by default) does exactly this:
ssh-copy-id user@hostname.example.com
copies the public key of your default identity (use -i identity_file for other identities) to the remote host.
The default identity is your "standard" ssh key. It consists of two files (public and private key) in your ~/.ssh directory, normally named identity, id_rsa, id_dsa, id_ecdsa or id_ed25519 (and the same with .pub), depending on the type of key. If you did not create more than one ssh key, you do not have to worry about specifying the identity, ssh-copy-id will just pick it automatically.
In case you do not have an identity, you can generate one with the tool ssh-keygen.
In addition, if the server uses a port different from the default one (22) you should use quotation marks in this way (source):
ssh-copy-id "user@hostname.example.com -p <port-number>"