Why is ufw firewall included in Ubuntu, when it is not enabled and pre-configured by default? Most users don't even know it is there, because no GUI frontend is provided.
5 Answers
Out of the box, Ubuntu ships with no TCP or UDP ports open, hence the belief that there's no reason to run Uncomplicated Firewall (ufw) by default. I agree, though, that having ufw disabled is a strange decision. My reasoning being that inexperienced users are feasibly going to install things like Samba, Apache and such like as they experiment with the system put before them. If they don't understand the implications of this, they will expose themselves to malicious bevaviour on the internet.
Example - I've got my laptop configured with Samba which is fine in my home network protected with WPA2. But if I take my laptop to a Starbucks, I might not think anything of it, but that laptop is now advertising my shares to all and sundry. With a firewall, I can restrict my samba ports to only my home server or peer devices. No need to worry as much now about who might be trying to connect to my laptop. Same goes for VNC, SSH, or a huge number of other useful services my laptop might be running, or trying to connect to.
Ubuntu takes a very on/off approach to certain elements of security, a philosophy I can't agree with. Security might be technically on or off, but by layering elements of security over one another, you end up with a better system. Sure, Ubuntu's security is good enough for a large number of use cases, but not all.
Bottom line, run ufw. Better safe than sorry.
Uncomplicated Firewall has a number of graphical front ends, but the simplest is Gufw.
sudo apt-get install gufw
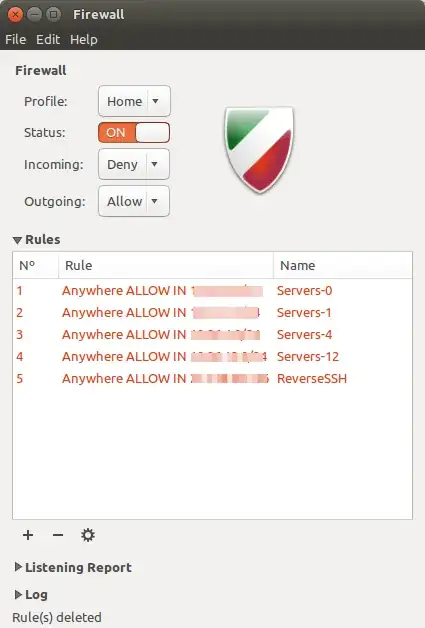
Here, I'm allowing all traffic from specific server VLANs in my corporate environment and I've added a rule to allow the necessary ports for a reverse SSH session to bounce off this machine.
- 11,229
In contrast to Microsoft Windows, an Ubuntu desktop does not need a firewall to be safe on the Internet, since by default Ubuntu does not open ports that can introduce security issues.
In general a properly hardened Unix or Linux system will not need a firewall. Firewalls (except of certain security problems with Windows computers) make more sense to block internal networks to the Internet. In this case local computers can communicate with each other over open ports which are blocks towards the outside by the firewall. In this case, the computers are intentionally opened up for internal communications which should not be available outside the internal network.
The standard Ubuntu desktop would not require this, hence ufw is not enabled by default.
- 29,406
In Ubuntu or any other Linux the firewall is a part of the base system and is called iptables/netfilter. It is always enabled.
iptables consists of a set of rules on what to do and how to behave when a packet if going out of coming in. If you want to explicitly block incoming connections from a specific IP, you will need to add a rule. Actually you don't need to do so. Relax.
If you want good security from anything, remember don't install random softwares from anywhere. It might screw up your default security settings.Don't run as root ever. Always trust the official repos.
I think what you wanted to ask was that if the UI is installed or not?
- 11,671
Also, gufw can provide a GUI front-end. (It isn't really more intuitive than ufw on the command line, to me, but it does give you a more visual reminder of what is there.) I agree that the firewall is not advertised well at present. If I were to guess, I'd say this is to prevent new users from shooting themselves in the foot.
- 23,540
Because: passwords or crypto-keys.
This is IMO the correct answer, and thus far, quite a different answer than the others. ufw is disabled by default for the convenience of the majority of Ubuntu users who know that passwords are an important form of protection to provide privacy and restricted control. The majority of Ubuntu users will "vet" software by installing from Ubuntu-approved repositories and be careful about other sources, in order to minimize risks in general, not just risk related to ports. By doing so they go a long way to minimizing the port-related risk which was already small because they use "normal" passwords and very small if they use hard-to-brute passwords or crypto-keys.
Some of the risks cited such as Samba file server, Apache HTTP server, SSH, VNC on a Starbucks (public) WiFi would typically be eliminated by hard-to-brute passwords on the host.
ufw "breaks" software, as a firewall should, which is the reason why it is disabled by default. To test this on a fresh install of Ubuntu, server A, install ssh and login from another machine, client B, on the same local network and you will see it works immediately. Logout. Then go back to server A and sudo ufw enable. Go back to client B and you will fail to ssh to server A.
- 10,039
