The information that you're referencing is obviously out of date.
To respond to some of the points you make in your question:
System > Preferences > Passwords and Encryption Keys.
This no longer exists in current versions of Ubuntu.
gpg --fingerprint
This is blank, because you have yet to generate or install any keys.
next rabbit hole is do this in terminal: gpg --full-generate-key
I get: Please select what kind of key you want: (1) RSA and RSA (2)
DSA and Elgamal (3) DSA (sign only) (4) RSA (sign only) (9) ECC (sign
and encrypt) default (10) ECC (sign only) (14) Existing key from card
Your selection?
really? can I just get the one I am required to have...
Encryption algorithms have evolved over time as new and more secure algorithms are created. Thus, the more secure ones will end up being the default. As a "default" selection, it's best practice to select the default options when generating GPG keys, especially if you don't know which one to select.
info at https://help.ubuntu.com/community/GnuPrivacyGuardHowto sez:
Please select what kind of key you want: (1) RSA and RSA (default) (2)
DSA and Elgamal (3) DSA (sign only) (4) RSA (sign only)
but default is different - which one is REALLY default?!? ...and what
is RSA and RSA about (some echo?)
From this link that you reference, it states the following:
-
If you are using GnuPG version 1.4.10 or newer, this will lead to a selection screen with the following options:
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
Select (1), which will enable both encryption and signing.
-
If you are using an older version, the selection screen will have the following options:
Please select what kind of key you want:
(1) DSA and Elgamal (default)
(2) DSA (sign only)
(5) RSA (sign only)
This clearly shows that the default has changed simply because the version of GnuPG is different. Today the GnuPG version is even newer (currently 2.4.4 on default installation of Ubuntu 24.04). Thus, it suggests that the default algorithm may be different as well.
Generate / Publish / Import to Launchpad
It sounds like you want to sign the Ubuntu Code of Conduct and it's requiring you to import your GPG key. There are many tutorials on AskUbuntu as well as the internet. Here's a summary:
Generate GPG key
$ gpg --full-generate-key
gpg (GnuPG) 2.4.4; Copyright (C) 2024 g10 Code GmbH
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Please select what kind of key you want:
(1) RSA and RSA
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
(9) ECC (sign and encrypt) default
(10) ECC (sign only)
(14) Existing key from card
Your selection?
Hit Enter to select the default selection:
Please select which elliptic curve you want:
(1) Curve 25519 *default*
(4) NIST P-384
(6) Brainpool P-256
Your selection?
Hit Enter again for the default selection:
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0)
You need to make a decision about how long the key should be valid for. This is a personal choice, but let's say two years. So enter 2y:
Key expires at Sun 28 Mar 2027 06:59:29 PM PDT
Is this correct? (y/N)
Enter y and Enter to confirm your choice:
GnuPG needs to construct a user ID to identify your key.
Real name:
Enter your real name, email address, and a comment if you want:
Real name: John Smith
Email address: johnsmith@example.com
Comment:
You selected this USER-ID:
"John Smith <johnsmith@example.com>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit?
If correct, hit O to confirm:
A pop-up window will appear for you to enter a passphrase. Enter a very secure passphrase and click OK. Your new key will be generated:
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
gpg: directory '/home/mike/.gnupg/openpgp-revocs.d' created
gpg: revocation certificate stored as '/home/mike/.gnupg/openpgp-revocs.d/C171EB28F0FE3AE0D8B3B3BA3582ED26FB81BDF8.rev'
public and secret key created and signed.
pub ed25519 2025-03-29 [SC] [expires: 2027-03-29]
C171EB28F0FE3AE0D8B3B3BA3582ED26FB81BDF8
uid John Smith <johnsmith@example.com>
sub cv25519 2025-03-29 [E] [expires: 2027-03-29]
You can list your keys with the following:
$ gpg --list-keys
/home/mike/.gnupg/pubring.kbx
-----------------------------
pub ed25519 2025-03-29 [SC] [expires: 2027-03-29]
C171EB28F0FE3AE0D8B3B3BA3582ED26FB81BDF8
uid [ultimate] John Smith <johnsmith@example.com>
sub cv25519 2025-03-29 [E] [expires: 2027-03-29]
Publish your GPG key
Next, you'll want to publish your key to a keyserver.
You'll first need your key ID, which can be seen in the above output. This output is showing the long version of the key ID, but all you need is the short version. This is the last eight characters of the long version key ID, which is hexadecimal. In this example, it's FB81BDF8.
To publish, run the following command and substitute your actual key ID:
gpg --send-keys --keyserver hkp://keyserver.ubuntu.com FB81BDF8
To confirm your key is in the keyserver, run the following and substitute the email used when generating the key:
gpg --keyserver hkp://keyserver.ubuntu.com --search-key 'johnsmith@example.com'
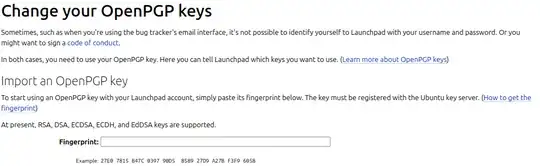
Import GPG key to Launchpad account
Next, import your key to Launchpad. This requires the fingerprint, which can be gathered as follows:
$ gpg --fingerprint
gpg: checking the trustdb
gpg: marginals needed: 3 completes needed: 1 trust model: pgp
gpg: depth: 0 valid: 1 signed: 0 trust: 0-, 0q, 0n, 0m, 0f, 1u
gpg: next trustdb check due at 2027-03-29
/home/mike/.gnupg/pubring.kbx
-----------------------------
pub ed25519 2025-03-29 [SC] [expires: 2027-03-29]
C171 EB28 F0FE 3AE0 D8B3 B3BA 3582 ED26 FB81 BDF8
uid [ultimate] John Smith <johnsmith@example.com>
sub cv25519 2025-03-29 [E] [expires: 2027-03-29]
In this example, the fingerprint is C171 EB28 F0FE 3AE0 D8B3 B3BA 3582 ED26 FB81 BDF8. You want to copy/paste your key's fingerprint into the fingerprint box on your profile page for your Launchpad account.
Useful links
GPG manpage
OpenPGP Key Management
Publish generated key to Launchpad
How do I check if my OpenPGP key is in the Ubuntu keyserver?
GnuPG : representations of key IDs and fingerprints
