Before proceeding I don't want to disable the Secure Boot option. I need a solution, not a workaround.
I have a humble setup using dnsmasq and the dnsmasq built-in tftp to give me a PXE server. I am trying to boot Ubuntu 22.04.
Setup:
I followed the official Ubuntu tutorial.
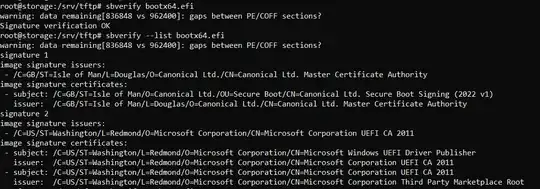
Initially I had problem with bootx64.efi as the NUC reported a boot violation, but the trick was to basically use the bootx64.efi.dualsigned to create the bootx64.efi. This is the result of sbverify on bootx64.
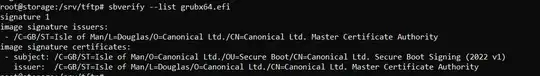
This solved the problem of boot policy violation and the pxe boot process successfully starts grub. I don't know how as the sbverify fails on this file.
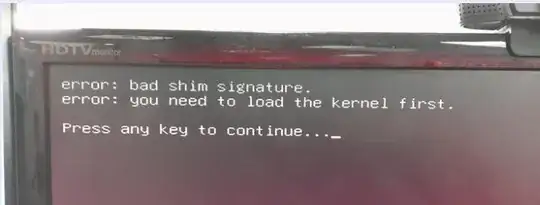
After I select from grub which ISO to run this is the error message I get
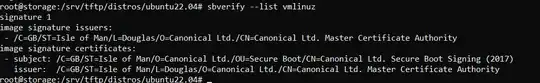
I don't know if this is the problem with grub or the actual signature of vmlinuz.
Without turning off Secure Boot how do I sign the kernel image with the correct and update signature or the grubx64.efi to make this work? Is there a way to do this with sbattach command (don't I need the actual public certificate for that) where can I find this certificate?