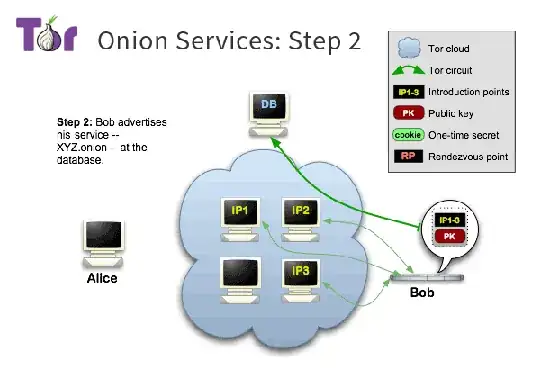
Currently working on a Tor study, I would have a question regarding the tor hidden services.
I read lot of technicals papers to better understand the tor working on this point, like these good articles: The Tor dark net: https://www.cigionline.org/sites/default/files/no20_0.pdf Content and popularity analysis of Tor hidden services: http://arxiv.org/pdf/1308.6768.pdf
But I couldn't get a clear answer to my interogations.
So the question is simple, I would like to know if it's possible, from a relay node, to sniff the traffic to get the onions address accessed through this node ?
In this case, the traffic is fully end to end encrypted, but is it only the data that are encrypted, or the onions address also ? For me, the onion address is a metadata, and not usefull information, so maybe it's not encrypted and we could get these metadatas ?
Thanks in advance for your explanations.