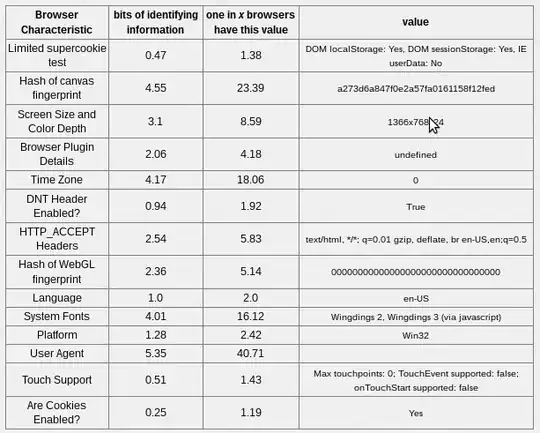
Yesterday I put some effort into getting the best "score" I can on Panopticlick. The following is my result:
I did several things to get the lowest numbers for "unique in x browsers".
- I looked up what the most common screen resolution is and set my browser to it. It's not the default setting of the TOR browser though.
- I've tried several user agent strings and it seems an empty string is way better than others.
- I deactivated WebGL, so that the WebGL canvas thing cannot be used.
- I got an addon to block HTML5 canvas and that asks me whenever someone tries to use HTML5 canvas on a site - shocking how often that is! But when I use it consequently on panopticlick, the test stops working at the last step, not letting me see the results, so that is not included in the screenshots. (Is there a better way to test my "uniqueness" somewhere?)
- I can deactivate the JS, but then I'd not see the information about all the things, which can be exploited when I have JS on, so that's also not in the screenshot.
However, despite all this effort, it seems I am still unique in 145k browsers. If I am still a unique profile, then all the confusion created by the TOR network is for naught, if someone really wanted to track me. If I multiply those "unique in x browsers" numbers together, I'd get the combined "uniqueness" when someone considers really all of the listed things there. The number is still sooooo high, I am still far from a not unique fingerprint. Now the question is:
Can I still improve this? If so, how?
And for everyone else I hope you have use for this configuration and that it helps you.