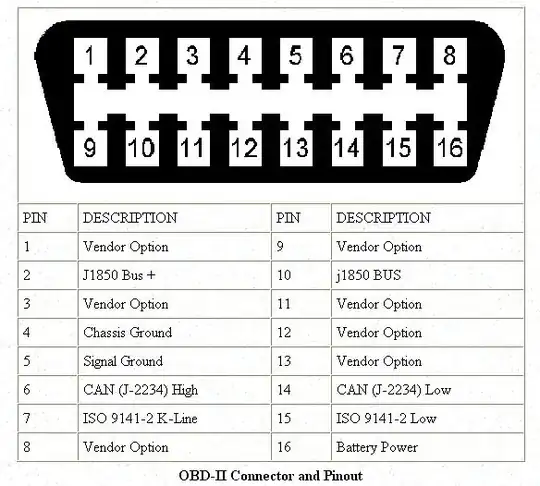
You would need to "Re-Engineer" an adapter once you accomplish "Disabling" your OBD-2 port. How you do that, is honestly up to your judgement. Depending on the vehicle they also have factory ports in very odd locations. Nissan, Toyota and a few European brands are known for this. Vehicle hacking is becoming a real thing that people DO have to worry about.
I attend Defcon and last year they added their car hacking village. Here are some videos about it. These guys REALLY know how this stuff works. I'm currently working on my own project because of these guys.
Car Hacking
They also explain a little bit about how to protect yourself correctly from being a victim.
As far as changing your pins to thwart a thief's attempts at getting into a car or to damage their tool. Most of the car hackers out there and things I've seen on darknet websites all use Rasberry Pi type devices WHICH use self correcting signal. It probably wouldn't even work if you did that. You'd essentially just be doing it for no reason or for your own reassurance. As someone who works with security and have been for years; There isn't much you can do.
What I would suggest is disable your keyless entry (The other guy mentioned that). You could disable the engine bay factory port. If you have GPS, disable that because COM systems are why Chrysler recalled millions of cars. These are honestly the only options you could within reason, use to secure your vehicle.
Also, it seems a bit like you don't fully understand how involved this process is and how long it takes to "Hack" a vehicle. They need entry to the vehicle first. They then need to apply their method of "hacking" to the car. Then manage to get away with this. Every make and model is different and there are no universal "tools" for this on the open market, or black market. I do analytics for work and keep up to date with this as much as possible. They would essentially have to research and engineer a tool for a specific Make and model for it to work efficiently. That takes MONTHS. Unless you own a contract with the manufacturer.
To essentially answer what you're asking.
Will switching the pins damage their tool
Most likely no. Especially with today's modern circuit boards and their processors that can route electrical signal if data collision occurs. You'll find this a lot in networking equipment.
What else can you suggest
All I can suggest is to disable your keyless entry, disable the engine bay factory ECU plug, and any COM systems that can be accessed wirelessly. Quite a few CAN data bus systems are implementing 802.11 into their vehicles and that's just another attack vector. If you have a really nice modern car, you might have something like that in your car. My Hyundai Genesis uses 802.11n and connects directly to the CAN from the radio.
Lastly, unless you're driving a $250,000 car I don't think you should worry yourself too much unless you just want a project.
Defcon Website
There is the defcon website. I hope I gave something that can help you!