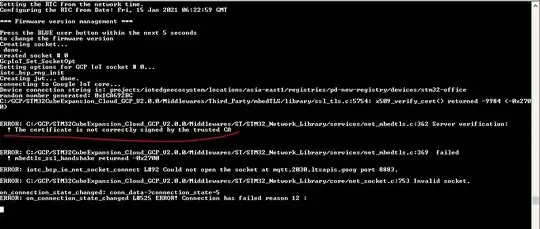
I am trying to make X-CUBE-GCP sample application SDK working. I am not able to connect to GCP cloud because of repetitive error - "The certificate is not correctly signed by the trusted CA".
I tried to check the certificate validity using openssl command and getting proper response as well-
$ openssl crl2pkcs7 -nocrl -certfile globalsign.pem | openssl pkcs7 -print_certs -noout
subject=OU = GlobalSign Root CA - R2, O = GlobalSign, CN = GlobalSign
issuer=OU = GlobalSign Root CA - R2, O = GlobalSign, CN = GlobalSign
subject=C = US, ST = New Jersey, L = Jersey City, O = The USERTRUST Network, CN = USERTrust RSA Certification Authority
issuer=C = US, ST = New Jersey, L = Jersey City, O = The USERTRUST Network, CN = USERTrust RSA Certification Authority
$ openssl x509 -enddate -noout -in globalsign.pem
notAfter=Dec 15 08:00:00 2021 GMT
Further, I am very closely following full SDK documentation and sure that all steps mentioned as per release document is being followed. Please help me resolve the issue.