This sounds very very much like an A/B problem to me. You want to protect data in such a way people won't suspect that it's sensitive data.
The easiest way to hide data is to just encrypt it using gpg, TrueCrypt, LUKS, or similar encryption utility.
Now, you could use steganography, but that isn't exactly the best idea because the concept of "security by obscurity" still comes into play. Any determined enough attacker will still be able to extract the file or at least find it ("why does this person have a 10GB image or a corrupt MP4? It might be hiding data!"). You're relying on security by obscurity, which is always a bad idea.
Instead, if you want to save something and keep plausible deniability, you just need to make sure that the data looks random and has no headers. LUKS/cryptsetup has an option (--header) that allows you to store the LUKS headers separately from the data (say, on a USB drive you always carry on you), so any attacker using file will only see it as random data. And, if you suspect someone's closing in, just conveniently "lose" the drive.
If you're really paranoid, you can always use hidden volumes in LUKS, which will allow you to have a fake outer volume as well as a more secret inner volume. Why would this be useful? Case in point:
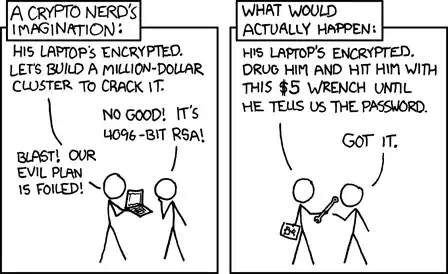
Comic borrowed from XKCD
Even if you're subject to rubber-hose cryptanalysis, you can just give away the outer (non-secret) volume password with only trash data. And, if you've already destroyed the header drive (or didn't take it from its safe place), it's impossible to decrypt and is effectively just a collection of random data.
TL;DR: Don't try steganography. Instead, just remove the encryption header to make it look like random data. If you're really paranoid, make an additional "hidden" volume just to be safe. Your encrypted file won't be cracked because that'll take literally millions of years with specialized equipment. If you get caught/tortured for the password, you can just give a "fake" password to non-important data. Either way, you get 2FA, plausible deniability, and the ability to destroy one of the factors quickly and efficiently.
Or, you can just ignore all of that and just have a normal encrypted file. To counter your comment:
Displaying it as being encrypted shows that it has precious content and is therefore more subject to be cracked by expensive ad hoc hardware.
Encryption is really common nowadays. Almost every smartphone out there has encryption on it. Does every smartphone have precious/sensitive content? Good encryption would take millions of years and hundreds of thousands of dollars to crack with very specialized equipment, it's infeasible to try to crack data just "on a suspicion." True, you might get national secrets, but you might just as easily get some cat pictures (and the latter is far more likely). As the title text for the above XKCD says:
Actual actual reality: nobody cares about his secrets.
