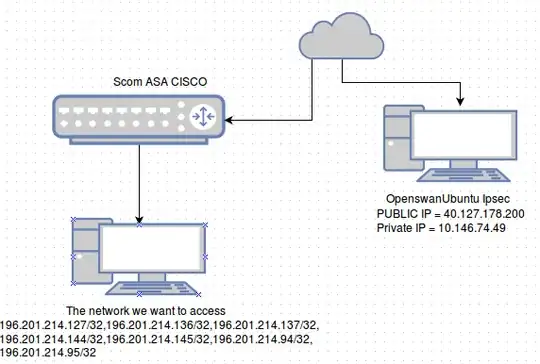
I've tried a week without any success to setup IPsec ESP authentication via a CISO ASA. This is the topology I'm trying to achieve
 .
.
I want to connect to the network which is on the back of CISCO from the Ubuntu IPsec client machine itself. The Ubuntu client has only one eth0 interface.
On the CISCO both the server and the peer IP is set to the Ubuntu clients public IP.
Here are my confs:
ipsec.conf
============================
config setup
nat_traversal=yes
virtual_private=%v4:10.0.0.0/8,%v4:192.168.0.0/16,%v4:172.16.0.0 /12,%v4:196.201.214.0/24
oe=off
force_keepalive=yes
plutostderrlog=/var/log/openswan.log
protostack=netkey
keep_alive=60
include /etc/ipsec.d/*.conf
============================
ipsec.conf
===========================
conn scom
authby=secret
auto=start
keyexchange=ike
ikelifetime=28800s
ike=3des-sha1;modp1024
phase2alg=aes128-sha1;modp1024
pfs=no
type=tunnel
aggrmode=no
compress=no
forceencaps=yes
left=10.146.74.49 (INternal IP Ubuntu openswan client)
leftid=10.146.74.49
leftsubnet=40.127.178.200/32 (External IP ubuntu openswan client)
leftsourceip=40.127.178.200
leftnexthop=%defaultroute
right=196.201.212.240 (Ciso ASA public IP)
rightsubnets={196.201.214.xx/32,196.201.214.xpx/32,196.201.214.xax/32,196.201.214.xxx/32,196.201.214.xjx/32,196.201.214.xxy/32,196.201.214.sss/32}
With this config the tunnel comes UP. But actually the left IP should be the Public IP of Ubuntu openswan client right? The tunnel fails If I put the public IP as the left parameter.
If the topology I mentioned has to work, what am I missing?