I have managed to get it to work using pam_exec:
Create a script to setup ecryptfs for all new users in /etc/security/ecryptfs:
#!/bin/bash
home=`eval echo ~$PAM_USER`
ecryptfs=/home/.ecryptfs/$PAM_USER/.ecryptfs
read password
if [ -d $ecryptfs ]; then
# ecryptfs is set
echo "Ecryptfs is already configured"
exit 0
elif [ `id -u` == 0 ]; then
# Setup ecryptfs and make home
umask 077
mkdir -p $home
group=`id -gn $PAM_USER`
chown $PAM_USER:$group $home
ecryptfs-setup-private -u $PAM_USER -l "$password" -b --nopwcheck
exit 0
else
# NOT ROOT
echo "Cannot login with 'su' for the first time"
exit 1
fi
Make sure the script is executable:
sudo chmod a+rx /etc/security/ecryptfs
Add entry to execute it with pam_exec on auth:
sudo vim /etc/pam.d/common_auth
Add the following lines:
auth required pam_exec.so expose_authtok /etc/security/ecryptfs
auth optional pam_ecryptfs.so unwrap
The pam_exec is set to required, because it will not setup ecryptfs if the script doesn't run as root. This is the case if su is used from a non-root user. So if ecryptfs is not setup and su is used (that is when the user attempts to login for the first time using su) then his will get refused. As such we ensure that the user cannot login without an ecryptfs setup.
Create another script to populate the home directory in place of pam_mkhomedir
sudo vim /etc/security/mkhome
This script will copy everything in /etc/skel if the file .donotremove doesn't exist.
#!/bin/bash
cd ~
if [ ! -f .donotremove ] ; then
echo Copying /etc/skel
cp -ra /etc/skel/* ~
touch .donotremove
fi
Also make sure this file is executable:
sudo chmod a+rx /etc/security/mkhome
Add another entry to execute this script on a session
sudo vim /etc/pam.d/common_session
Add the following lines:
session optional pam_ecryptfs.so unwrap
session optional pam_exec.so seteuid /etc/security/mkhome
Now LDAP users can login and have an ecryptfs encrypted home directory.
Update
Instead of editing the files in /etc/pam.d directly (which is generally not recommended), it is better to apply the settings as a PAMConfig profile.
Just paste this code into a new file /usr/share/pam-configs/ecryptfs-nonlocal:
Name: Enable EcryptFS for users from remote directories such as LDAP.
Default: no
Priority: 0
Conflicts: ecryptfs-utils
Auth-Type: Additional
Auth-Final:
required pam_exec.so expose_authtok /etc/security/ecryptfs
optional pam_ecryptfs.so unwrap
Session-Type: Additional
Session-Final:
optional pam_ecryptfs.so unwrap
optional pam_exec.so seteuid /etc/security/mkhome
Password-Type: Additional
Password-Final:
optional pam_ecryptfs.so
And then run pam-auth-update:
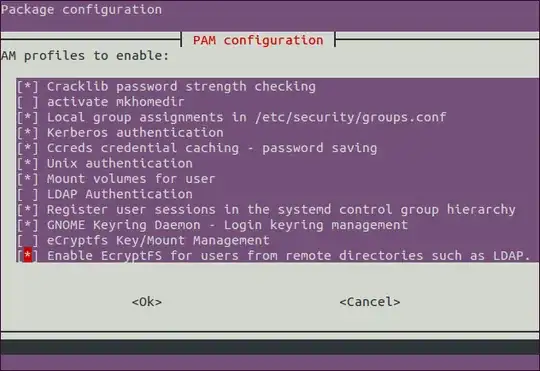
Check Enable EcryptFS for users from remote directories such as LDAP. and make sure that eCryptfs Key/Mount Management is unchecked. Leave all other options up to your preferences.
This will make sure that relevant configs in /etc/pam.d are applied and that they stay there.
